- Try to secure CI/CD pipeline from attacks and understand the limitation
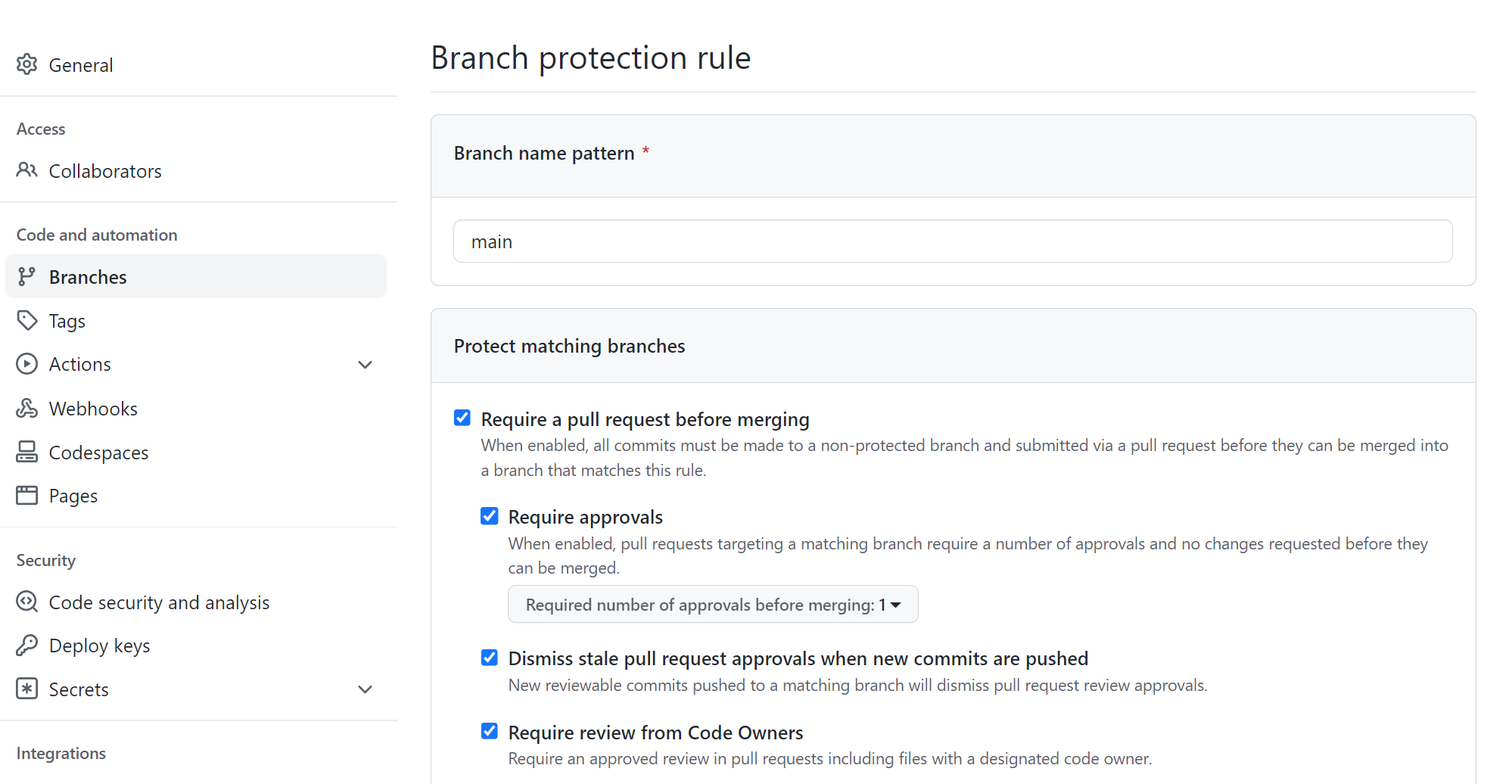
- Configure Branch Protection
- Caution: GitHub Free version doesn't support it. You need to use GitHub Pro or Team
- Configure OIDC, then try keyless between GitHub actions and Google Cloud
- Enter GitHub Actions using Tailscale and reverseshell (The procedure is in the slide)
- Steal Google Service Account Token in the keyless environment
- Steal IaC's CI(read) token, then see tfstate file on Google Storage
- Then Consider what role CI should have to do
Least Privilegepolicy
- Then Consider what role CI should have to do
- Target Repository:
devenv-security-iac
- Target Repository:
devenv-security-iac - Rename
google_actions_oidc.tf_togoogle_actions_oidc.tf(devenv-security-iac/terraform/training-project/)- Change these lines. (Replace
<github org or name>to Your Github Org or Name)# You need to modify this value locals { app_repo_name = "<github org or name>/devenv-security-app" iac_repo_name = "<github org or name>/devenv-security-iac" } - It enables Workload Federation
- Change these lines. (Replace
- Modify Iac's Actions Workflows
devenv-security-iac/.github/workflows/apply.yaml,devenv-security-iac/.github/workflows/plan.yaml- Uncomment
id-token: 'write' - Comment out
credentials_json - Uncomment
workload_identity_provider: 'projects/<Project Number>/locations/global/workloadIdentityPools/training-pool/providers/training-provider'- Replace
<Project Number>to Your Project Number
- Replace
- Uncomment
service_account: 'iac-actions-cd@<Project ID>.iam.gserviceaccount.com'- Replace
<Project ID>to Your Project ID
- Replace
- Uncomment
- You can do the same thing to App too.