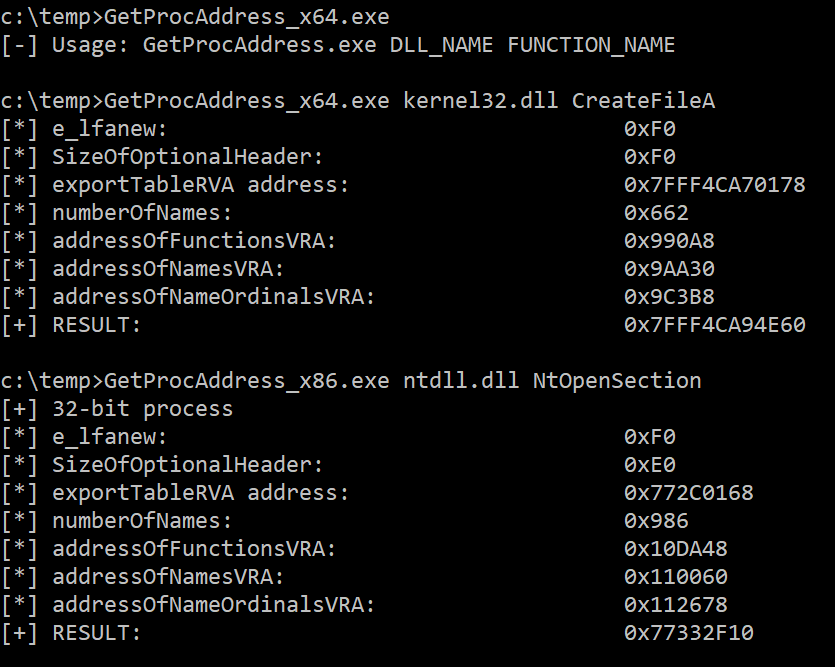
It works like the GetProcAddress WinAPI: it takes a DLL handle and a function name or ordinal, walks the PEB structure and returns the function address.
It only uses the NtReadVirtualMemory native API call, without using structs.
It works in both 32-bit and 64-bit processes. You can test this using the binaries in the Releases section:
-
Sektor7's Malware Intermediate course by reenz0h implements this code in C++
-
PE File Format Offsets: http://www.sunshine2k.de/reversing/tuts/tut_pe.htm